You will get hacked, fooled or beached at some point. Expect that, plan for that and move on from that.
We have to plan for the sinking of the vessel not just the floating of it.
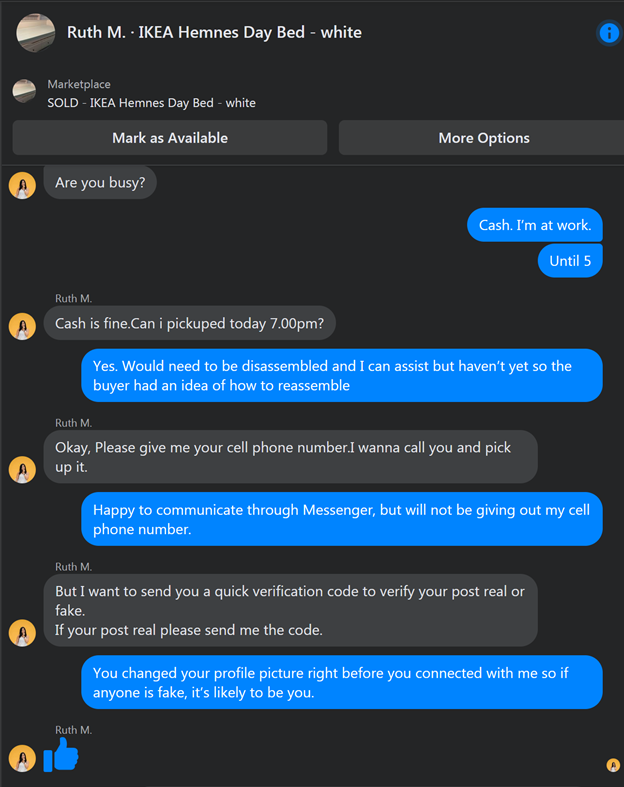
I sold a daybed on Facebook Marketplace recently. The first two responders wanted me to give them my cell phone number to validate that I was real. Same scam, one was chatty and sloppy in their spelling and grammar. The other was clear and concise. Both were fake and were obviously working from the same playbook. Compromise my cellphone so they could gain access to it and my associated accounts.
We had someone reach out for help a few months ago who had fraudulent transactions occurring in their personal finances. The culprit? A compromised cellphone. How compromised? The criminals were listening in and gained access to the new account that was set up to stop the fraud and only discussed via a phone call made from that cellphone. No emails, just voice!
Essentially these are professionals looking to separate you and me from our data or from our finances. Recently a hacking organization was caught posing as a cybersecurity firm to hire new hackers. I guess staffing challenges cross over to the criminal world too. Bottom line is that if these organizations are this serious and professional about getting access and being successful in their endeavours we all need to be more serious and professional as well.
Simple game plan to start with:
- Partner with outside professionals. Make them prove how they protect themselves and how they define success.
- Have a plan that factors in a Recovery Point Objective (RPO) and a Recovery Time Objective (RTO). You need to know what you’d like to have as level of functionality and how long it’ll take to get there in the event that you lose access to your systems or data – for any reason. This will include backup and disaster recovery solutions but should also provide for business continuity.
- Test the above at some set interval but no less than annually (consider quarterly with at least weekly reporting).
- Multi-factor the World! If you can turn on 2FA or MFA, do it!
- Get a managed password manager. Heps make passwords more random, harder to crack and mitigates the risk of any keylogging software being used against you. The managed ones are better because you can implement organization-wide and provide for employees. Makes the first day and last day of a staff member’s tenure a lot less stressful (for you and them).
- Stop being cheap. Free is NOT your friend in the world of cybersecurity. Look at the cost of loss, breach, reputation and downtime. Not at the cost of tools and services in a vacuum devoid of the worst day.
- Slow down. Most mistakes happen when we are in a hurry. Injuries, speeding tickets, phishing email links clicked…
Want to get serious? Contact us and we’ll perform a third party assessment to see how safe you really are and where the gaps are.
1-866-755-4486



